You are a network techn ician, study the exhibit carefully. All multilayer switches are running PIM sparse mode. Host CKB and Host CKF are sending IGMPv2 join messages to their respective multilayer switches. Which description is correct?()A. Switches 1,
题目
You are a network techn ician, study the exhibit carefully. All multilayer switches are running PIM sparse mode. Host CKB and Host CKF are sending IGMPv2 join messages to their respective multilayer switches. Which description is correct?()

A. Switches 1, 2, 3, and 6 will part icipate in the multicast tree once pruning has taken place.
B. Switches 2 and 6 will participate in the multicast tree once pruning has taken place.
C. Switches 1, 2, 3, and 6 will participate in the multicast tree.
D. The multicast server is the rendez vous point of the multicast tree.
相似考题
更多“You are a network techn ician, study the exhibit carefully. All multilayer switches are ru ”相关问题
-
第1题:
You are a network administrator for your company. All servers run Windows Server 2003. A server namedServer34 runs an application named App1.Users report that App1 is performing slowly. You suspect that an unauthorized application is installed on Server34.You run the netstat command and examine the output, as shown in the exhibit. (Click the Exhibit button.)You need to identify the unauthorized application by using the output from the netstat command.Which tool should you use to identify the application? ()

A. Performance console
B. System Monitor
C. Network Monitor
D. Task Manager
参考答案:D
-
第2题:
A new switch is being installed in the Ezonexam network and you have been assigned the task of connecting it to an existing switch. In doing this, you want to set up the VLAN Trunking Protocol so that VLAN information can be passed between the switches. Which of the following must you do to accomplish this? (Choose all that apply).
A.You must set each end of the trunk line to IEEE 802.1e encapsulation.
B.You must set the same VTP management domain name on both switches.
C.You must set all ports on the two switches as access ports.
D.You must configure one of the switches as a VTP server.
E.You must use a rollover cable to connect the two switches.
正确答案:BD
解析:Explanation:ThefollowingdescribeswhatisneededinordertocorrectlysetupVTP:IncorrectAnswers:A.TheencapsulationcanbeeitherISLor802.1Q,andneedtomatchateachendofthetrunk.C.PortsmustonlybeassignedtoVLANS.Oncethatisdoneandthetrunkisupandrunning,theVLANinformationwillbepassedbetweentheswitches.E.AregularCAT5cableisusedtoconnecttheswitches,assuming10/100Ethernetisused. -
第3题:
Refer to the exhibit. You have a non-Cisco switch that is not communicating properly while connected to the distribution-layer Cisco switching fabric.Which two best-practice actions can you take to overcome this problem? ()(Choose two.)
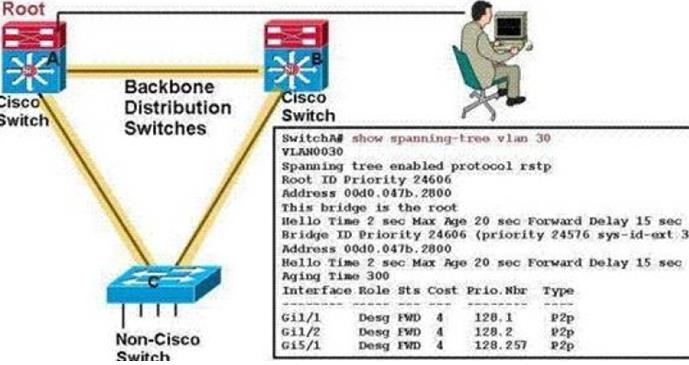
A. Turn off MST (802.1s) on all switches.
B. Turn on MST (802.1s) on all switches.
C. Turn on RSTP (802.1w) on all switches.
D. Turn off RSTP (802.1w) on all switches.
参考答案:B, D
-
第4题:
Refer to the network of Layer 3 switches in the exhibit. The RPI Multi cast Server only multicasts to hosts connected to multilayer switches 5 and 6. The CMU Multicast Server multicasts to hosts on multilayer switches 1 - 6. Given the number of configuration steps involved, what is the most efficient way to configure the net work while meeting the requirements for multicast data flow? ()

A. Configure each switch with PIM sparse mode and a separate instance of PIM dense mode.Specify switch 1 as the root for the RPI Multicast Server. Specify switch 2 as the root for the CMU Multicast Server.
B. Configure each switch with PIM sparse mode and a separate instance of PIM dense mode. Leave each multicast server as the root of its own multicast tree.
C. Configure each switch with PIM sparse - dense mode. Configure switch 3 as a ren dezvous point for the RPI multicast stream.
D. Configure each switch with PIM sparse mode and a separate instance of PIM dense mode.Allow the switches to elect their own root for each multicast tree.
E. Configure each switch with PIM sparse mode.
F. Configure each switch with PIM dense mode.
参考答案:C
-
第5题:
Refer to the exhibit. A network technician is asked to design a small network with redundancy. The exhibit represents this design, with all hosts configured in the same VLAN. What conclusions can be made about this design?()

A.The design will function as intended
B.Spanning-tree will need to be used.
C.The router will not accept the addressing scheme.
D.The connection between switches should be a trunk.
E.The router interfaces must be encapsulated with the 802.1Q protocol.
参考答案:C
-
第6题:
You are the network administrator for The network consists of a single Active Directory domain named The domain contains 352,000 Windows 2000 Professional computers. You install and configure Software Update Services (SUS) on a server named TestKing3. You need to scan all computers in the domain to find out whether they have received all approved updates that are located on the SUS server. What should you do?()
- A、On a server, install and run the mbsacli.exe command with the appropriate configuration switches.
- B、On a server that runs IIS, install and configure urlscan.exe.
- C、Edit and configure the Default Domain Policy to enable the Configure Automatic Updates policy.
- D、From a command prompt on TestKing3, run the netsh.exe command to scan all computers in the domain.
正确答案:A -
第7题:
our network consists of a single Active Directory domain. All network servers run Windows Server 2003 Service Pack 2 (SP2). The network contains a single subnet. The network connects to the Internet by using a network address translation (NAT) device. You deploy a new DHCP server named Server1. You create a scope as shown in the exhibit. (Click the Exhibit button.) You need to ensure that client computers can connect to the Internet. What should you do?()
- A、Add a Router scope option.
- B、Enable conflict detection on the DHCP server.
- C、Remove the WINS/NBT Node Type scope option.
- D、Configure the scope to respond to a BOOTP request only.
正确答案:A -
第8题:
You are the network administrator for Company.Company has just upgraded its network switches from 10 Mbps to 100 Mbps. After the upgrade, you findthat the 100 Windows 2000 Professional computers on the network are still communicating at only 10Mbps. Company uses NWLink as the only network protocol.You want to enable the computers to communicate at 100 Mbps.What should you do?()
- A、Replace the network adapters with 10/100 Mbps network adapters.
- B、Enable TCP/IP on all of the computers on the network.
- C、Configure the NWLink frame type of the network adapters to be Ethernet II.
- D、Configure the NWLink frame type of the network adapters to be Ethernet 802.3.
正确答案:A -
第9题:
单选题When is a switched network that is running the Spanning Tree Protocol considered to be fully converged?()Awhen all switches have the same BID as the root switch
Bwhen all switches have received the MAC address of each neighboring switch
Cwhen every enabled switch port has been assigned a unique identifier
Dwhen every operating switch port is in either the blocking or forwarding state
Ewhen all switches are in either client, server, or transparent mode
正确答案: A解析: 暂无解析 -
第10题:
单选题During testing of network redundancy in a fully meshed enterprise campus, a problem has been reported. Both distribution multilayer switches are fully configured for redundancy; clients operate normally when the primary multilayer distribution switch is operating. All clients drop connections outside of their respective access layer group when the primary distribution switch is shut down and the secondary distribution switch is still operational. Additional information indicates that the secondary distribution switch is able to ping major corporate and Internet locations. Which item would be the best point of troubleshooting for this connectivity issue? ()Aclient network configuration
BVLAN mapping
Cinter-switch trunk configuration
DUDLD configuration
Efirst-hop redundancy protocol
正确答案: D解析: 暂无解析 -
第11题:
单选题You are using VTP version 2 in your network to transport VLAN information between switches. When adding a switch to the network that has been used in the lab previously, you notice that a lot of the existingVLANs have been deleted or replaced with other names. What can you do to prevent this from happeningin the future, without losing all VTP features that you are using today?()Aconfigure a hard-to-guess VTP domain name
Buse a hard-to-guess VTP password
Cuse VTP transparent mode
Dimplement VTP version 3
正确答案: D解析: 暂无解析 -
第12题:
单选题Your network contains a DNS server named DC1 that runs Windows Server 2008 R2.The network uses a network ID of 10.1.1.0/24.You open the DNS console on Server1 as shown in the exhibit.(Click the Exhibit button.)You need to ensure that all client computers can resolve the IPv4 addresses of computers on the network to fully qualified domain names (FQDNs).What should you do??()ADelete the . (root) zone.
BCreate a zone named 10.1.in-addr.arpa.
CCreate a zone named 1.1.10.in-addr.arpa.
DConvert the 10.1.1.in-addr.arpa zone to a standard primary zone.
正确答案: D解析: 暂无解析 -
第13题:
Your network contains a server named Server1 that runs Windows Server 2008 R2. The network contains multiple subnets.An administrator reports that Server1 fails to communicate with computers on remote subnets.You run route.exe print on Server1 as shown in the exhibit. (Click the Exhibit button.)You need to ensure that Server1 can communicate with all computers on the network.What should you do?()

A. Disable IPv6.
B. Change the subnet mask.
C. Add a default gateway address.
D. Change the default metric to 100.
参考答案:C
-
第14题:
You are the network administrator for . All network servers run Windows server 20003, and all client computers run Windows XP Professional.A user named King manages an application server named Server25. One morning,King tries to log on to the network from Server 25. He receives the message shown in the Logon message exhibit.King notifies you of the problem. You open Active Directory Users and Computers and see the display shown in the Active Directory exhibit.You need to enable King to log on to Server 25. Your solution must require the minimum amount of administrative effort.What should you do?()


A. Enable the computer account for Server 25
B. Reset the computer account for Server 25.
C. Remove Server 25 from the domain, and then rejoin Server25 to the domain.
D. Delete the computer account for Server25, and then create a new account with the same name.
参考答案:A
-
第15题:
Refer to the exhibit. ROUTE.com has just implemented this EIGRP network. A network administrator came to you for advice while trying to implement load balancing across part of their EIGRP network. If the variance value is configured as 2 on all routers and all o ther metric and K values are configured to their default values, traffic from the Internet to the data center will be load balanced across how many paths? ()

A. 1
B. 2
C. 3
D. 4
E. 5
参考答案:C
-
第16题:
Refer to the exhibit. All multilayer switches are running PIM dense mode. Recipient A and Recipient B are sending IGMPv2 joi n messages to their respective multilayer switches. Which statement is true?()

A. The Multicast Server is the root of the multicast tree. Switches 1, 3, 4, and 5 will participate in the multicast tree once pruning has taken place.
B. The Multicast Serv er is the root of the multicast tree. Switches 4 and 5 will participate in the multicast tree once pruning has taken place.
C. Switch 3 is the root of the multicast tree. Switches 3,4, and 5 will participate in the multicast tree once pruning has taken place.
D. Switch 3 is the root of the multicast tree. Switches 1,3,4, and 5 will participate in the multicast tree once pruning has taken place.
E. Switch 1 is the root of the multicast tree. Switches 1,4, and 5 will participate in the multicast tree once pruning has taken place.
F. Switch 1 is the root of the multicast tree. Switches 1,3,4, and 5 will participate in the multicast tree once pruning has taken place.
参考答案:A
-
第17题:
You are an administrator of a switched network and your goal is to reduce some of the administrative overhead on your network. You plan on achieving this by configuring a new VLAN for each department in your network. However, you need to share the VLAN information across numerous switches throughout your network. Which of the following would allow you accomplish this?()
- A、STP
- B、GVRP
- C、SNMP
- D、VTP
- E、DHCP
正确答案:D -
第18题:
Your network contains a DNS server named Server1 that runs Windows Server 2008 R2.Root hints for Server1 are configured as shown in the exhibit. (Click the Exhibit button.)You need to add root hints to Server1.What should you do first?()
- A、Disable recursion.
- B、Delete the . (root) zone.
- C、Restart the DNS Server service.
- D、Remove all conditional forwarders.
正确答案:B -
第19题:
You are the network administrator for your company. The network consists of a single Active Directory domain named . All domain controllers run Windows Server 2003, and all client computers run Windows XP Professional. All client computer accounts are stored in the Computer container. A user named Peter reports that he cannot log on to the domain from his computer. Peter receives the logon message shown in the exhibit. Exhibit: Logon Message Your account is configured to prevent you from using this computer. Please try another computer. You need to enable Peter to log on. What should you do?()
- A、Create an account for Peter's computer in the Computers container.
- B、Grant the Log on locally user right to Peter's user account.
- C、Enable Peter's user account.
- D、Change the properties of Peter's user account so he can log on to any computer.
正确答案:D -
第20题:
单选题Refer to the exhibit. A network technician is asked to design a small network with redundancy. The exhibit represents this design, with all hosts configured in the same VLAN. What conclusions can be made about this design?()AThe design will function as intended
BSpanning-tree will need to be used.
CThe router will not accept the addressing scheme.
DThe connection between switches should be a trunk.
EThe router interfaces must be encapsulated with the 802.1Q protocol.
正确答案: C解析: 暂无解析 -
第21题:
单选题You are an administrator of a switched network and your goal is to reduce some of the administrative overhead on your network. You plan on achieving this by configuring a new VLAN for each department in your network. However, you need to share the VLAN information across numerous switches throughout your network. Which of the following would allow you accomplish this?()ASTP
BGVRP
CSNMP
DVTP
EDHCP
正确答案: D解析: 暂无解析 -
第22题:
单选题The Cisco MDS 9000 Series Multilayer SAN Switches can help lower the total cost of ownership of the most demanding storage environments. By combining a robust and flexible hardware architecture with multiple layers of network and storage-management intelligence, the Cisco MDS 9000 Series helps you build highly available, scalable storage networks with advanced security and unified management.What method does the Cisco MDS 9000 Series use to support trunking?()AISL
BVLAN Trunk
CVoQ
DEnhanced ISL
正确答案: B解析: 暂无解析 -
第23题:
单选题You have just created a new VLAN on your network. What is one step that you should include in your VLAN based implementation and verification plan? ()AVerify that different native VLANs exist between two switches for security purposes.
BVerify that the VLAN was added on all switches with the use of the show vlan command.
CVerify that the switch is configured to allow for trunking on the switch ports.
DVerify that each switch port has the correct IP address space assigned to it for the new VLAN.
正确答案: D解析: 暂无解析
